IT Great Falls - Why 66% of Montana SMBs Without Incident Response Plans Get Hit Hardest by Cyberattacks (And How IT Outsourcing Fixes This)
When a cyberattack hits your Montana business at 2 AM, who answers? For many, nobody. Without an incident response plan, the damage is often far worse.
Why 66% of Montana SMBs Without Incident Response Plans Get Hit Hardest by Cyberattacks (And How IT Outsourcing Fixes This)
When a cyberattack hits your Montana business at 2 AM on a Tuesday, who answers the phone? If you're like most small and medium-sized businesses across the Treasure State, the answer might be "nobody." That's exactly why businesses without incident response plans suffer the most devastating consequences when cybercriminals strike.
The numbers tell a sobering story: 43% of all cyberattacks specifically target small businesses, and when they hit, the impact is crushing. Half of all SMBs report that recovery takes 24 hours or longer, while 75% admit they couldn't continue operating if hit with ransomware. For Montana businesses operating in remote locations with limited local IT resources, these statistics become even more alarming.
What Is an Incident Response Plan (And Why Most Montana Businesses Don't Have One)
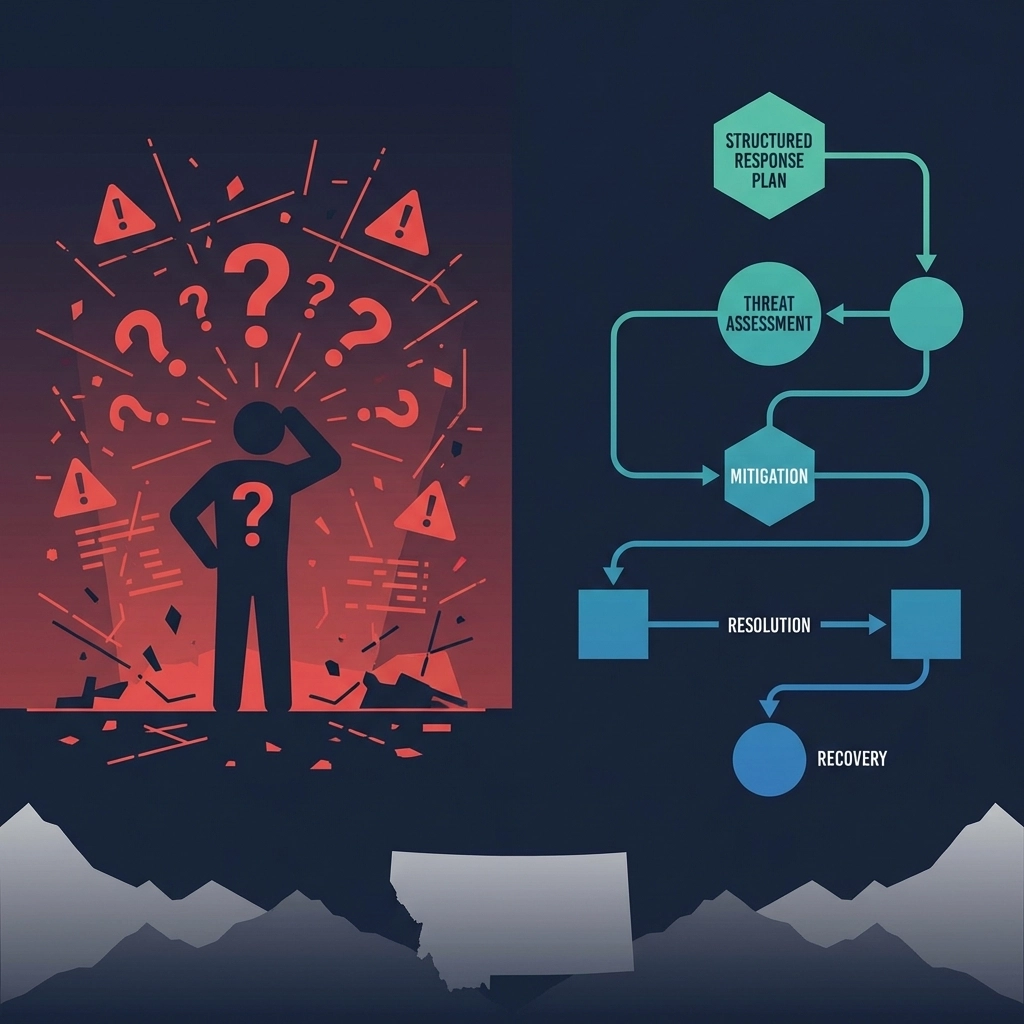
An incident response plan is your business's emergency playbook for cyberattacks. Think of it as your fire drill procedure, but for digital disasters. It outlines exactly who does what, when they do it, and how they coordinate during a security breach.
The plan typically includes immediate containment steps, communication protocols, evidence preservation procedures, and recovery timelines. Most importantly, it assigns specific roles to team members so nobody stands around wondering what to do while hackers are actively stealing your data.
Yet less than half of businesses with fewer than 50 employees have any security plan in place. In Montana, where many businesses operate with lean teams and limited resources, this percentage drops even further. The result? When attacks happen, businesses scramble to figure out basic steps like "Should we shut down the computers?" and "Who do we call first?"
Why Small and Medium-Sized Businesses Take the Hardest Hit
Cybercriminals deliberately target smaller businesses because they present the perfect combination of valuable data and weak defenses. Here's why Montana SMBs are particularly vulnerable:
Limited Internal Expertise: Only 15% of SMBs have hired internal IT staff or outsourced to a Managed Security Service Provider with sufficient expertise to develop robust cyber defenses. The remaining 85% rely on makeshift solutions that leave gaping security holes.
DIY Cybersecurity Approach: A staggering 74% of SMB owners handle cybersecurity themselves or rely on someone they know. Even more concerning, 49% admit they or their helper lack proper training. It's like performing surgery after watching a YouTube video.
Delayed Detection and Response: Without always-on monitoring, small businesses often discover breaches weeks or months after they occur. By then, attackers have had unlimited time to steal data, install additional malware, and plan their next moves.
Resource Constraints: Montana businesses face unique challenges with geography and talent availability. Finding local cybersecurity expertise in smaller communities like Great Falls, Helena, or Bozeman can be nearly impossible, forcing businesses to either go without or rely on inadequate solutions.

Essential Components of an Effective Incident Response Plan
A robust incident response plan contains six critical phases that transform chaos into coordinated action:
Preparation Phase: Establish your incident response team, define communication channels, and ensure everyone knows their role. For Montana businesses, this often means identifying which local and remote resources you'll activate during an emergency.
Identification and Detection: Deploy monitoring systems that can detect threats in real-time. This includes network monitoring, endpoint detection, and user behavior analytics that spot suspicious activities before they escalate.
Containment Strategies: Develop immediate and long-term containment procedures. Immediate containment might involve isolating affected systems, while long-term containment focuses on eliminating the threat entirely without disrupting critical operations.
Eradication and Recovery: Remove the threat completely and restore systems from clean backups. This phase requires verified clean backup systems and tested recovery procedures that actually work under pressure.
Lessons Learned: Document what happened, how you responded, and what you'll do differently next time. This creates a feedback loop that strengthens your defenses against future attacks.
Communication Protocols: Define who communicates with employees, customers, vendors, and potentially law enforcement or regulatory bodies. In Montana's tight-knit business communities, reputation management during a breach becomes especially critical.
Your Incident Response Checklist: 8 Steps Every Montana Business Needs
Here's a practical checklist you can implement immediately:
☐ Establish Your Response Team: Designate specific individuals for IT coordinator, communications lead, legal/compliance contact, and executive decision-maker roles.
☐ Create Communication Trees: List all internal and external contacts with current phone numbers, including your IT support provider, legal counsel, insurance carrier, and key vendors.
☐ Document Your Network: Maintain current network diagrams, asset inventories, and system dependencies so responders understand what they're protecting.
☐ Test Your Backup Systems: Verify that backups work and can be restored quickly. Many businesses discover their backups are corrupted only during an actual emergency.
☐ Define Decision Authority: Specify who has authority to shut down systems, authorize emergency expenses, and make public statements during an incident.
☐ Prepare Legal and Regulatory Contacts: Know your notification requirements for data breaches under Montana law and federal regulations affecting your industry.
☐ Create Communication Templates: Pre-write notification emails for employees, customers, and partners so you're not crafting messages while under attack.
☐ Schedule Regular Plan Reviews: Update your plan quarterly and conduct tabletop exercises twice yearly to ensure everyone remembers their roles.

How IT Outsourcing Transforms Your Incident Response Capabilities
For Montana businesses, partnering with experienced managed IT services providers changes everything about incident response. Here's how professional IT outsourcing addresses the most critical gaps:
24/7 Security Operations Center (SOC) Monitoring: While you sleep, trained security analysts monitor your systems for threats. When something suspicious happens, they're already investigating before you even know there's a problem.
Immediate Expert Response: Instead of frantically googling "what to do during a cyberattack," you have immediate access to incident response specialists who've handled hundreds of similar situations. They know exactly which steps to take in which order.
Advanced Threat Detection: Professional managed IT services Montana providers deploy enterprise-grade security tools that would be cost-prohibitive for individual small businesses. These systems use artificial intelligence and machine learning to spot threats that basic antivirus software completely misses.
Automated Containment and Recovery: Modern security systems can automatically isolate infected systems, block malicious traffic, and begin recovery procedures without waiting for human intervention. This cuts response times from hours to minutes.
Compliance Expertise: IT outsourcing partners understand the complex legal requirements around data breach notifications, forensic evidence preservation, and regulatory reporting that vary by industry and location.
Proven Recovery Procedures: Experienced providers have refined their recovery processes through real-world incidents. They know how to prioritize system restoration, minimize downtime, and get your business operating normally as quickly as possible.
Why Great Falls and Montana Businesses Choose Professional IT Support
Montana's geographic challenges make reliable IT outsourcing even more valuable. Local businesses in Great Falls, Billings, Missoula, and smaller communities face unique obstacles that professional managed IT services providers understand and address:
Remote Monitoring Capabilities: Distance becomes irrelevant when your IT partner can monitor and manage your systems remotely. Whether you're located in downtown Great Falls or a rural Montana community, you receive the same level of protection and response.
Understanding Local Business Needs: Montana IT support providers understand seasonal business patterns, economic cycles, and regulatory requirements specific to industries like agriculture, energy, tourism, and healthcare that drive the state's economy.
Cost-Effective Enterprise Security: By sharing costs across multiple clients, managed IT services make enterprise-level cybersecurity affordable for businesses that couldn't justify hiring full-time security specialists.
Scalable Response: Whether you're a 5-person accounting firm in Helena or a 50-employee manufacturing company in Great Falls, professional IT outsourcing scales to match your specific needs and budget.

Building Cyber Resilience in Big Sky Country
The reality is that cyberattacks are not a matter of "if" but "when" for Montana businesses. The question becomes: Will your business be ready with a coordinated response plan, or will you join the statistics of companies that suffer prolonged downtime, data loss, and reputation damage?
Effective incident response planning combined with professional IT support creates a security foundation that lets you focus on growing your business instead of worrying about the next cyber threat. When attacks do happen: and they will: you'll have the expertise, tools, and procedures necessary to minimize damage and restore operations quickly.
Your Montana business deserves the same level of cybersecurity protection as Fortune 500 companies. With the right incident response plan and IT outsourcing partnership, you can achieve exactly that level of protection without the enterprise-level budget.
Ready to protect your Montana business with professional cybersecurity services and incident response planning? Contact IT Great Falls today at 406-866-0128 or visit https://itgreatfalls.com to discuss how managed IT services can strengthen your cyber defenses.
Meta Title: Why 66% of Montana SMBs Without Incident Response Plans Get Hit Hardest by Cyberattacks | IT Great Falls
Meta Description: Most Montana SMBs lack effective incident response plans—discover why this makes them top cyber targets, the essentials to include in your IR plan, and how IT outsourcing keeps your business protected. Learn more from IT Great Falls.
Meta Image: 

No comments yet. Login to start a new discussion Start a new discussion